Setup NETVS
SCC Serviceaccounts will soon be deprecated
We are currently in the process of deprecating KIT-global service accounts in favor of NETVS-internal service accounts. We hope to provide updated documentation and migrations instructions soon. If you can afford to either wait or recycle existing service account, we urge you to do so.
Warning
If your organizational unit is managed by ATIS (Abteilung Technische Infrastruktur), this process will most likely not work for you, because ATIS adds another management layer on top of NETVS. Please contact ATIS for how to work with ACME.
Pre-Setup
- Create or request a service account
- Wait for at least an 1 hour for the identity management synchronisation
Assigning rights to the new service account
- Log in to NETVS (using your normal account).
- Go to https://netvs.scc.kit.edu/org/ou
- Select your OE, remember the »OE-Kurzbezeichnung«
- Make sure your account is listed as »OE-Betreuer«
- Go to https://netvs.scc.kit.edu/cntl/groups (click on »Gruppen« in the left navigation bar)
- Create a new group »Neue Gruppe anlegen«
- Important: Add the »OE-Kurzbezeichnung«

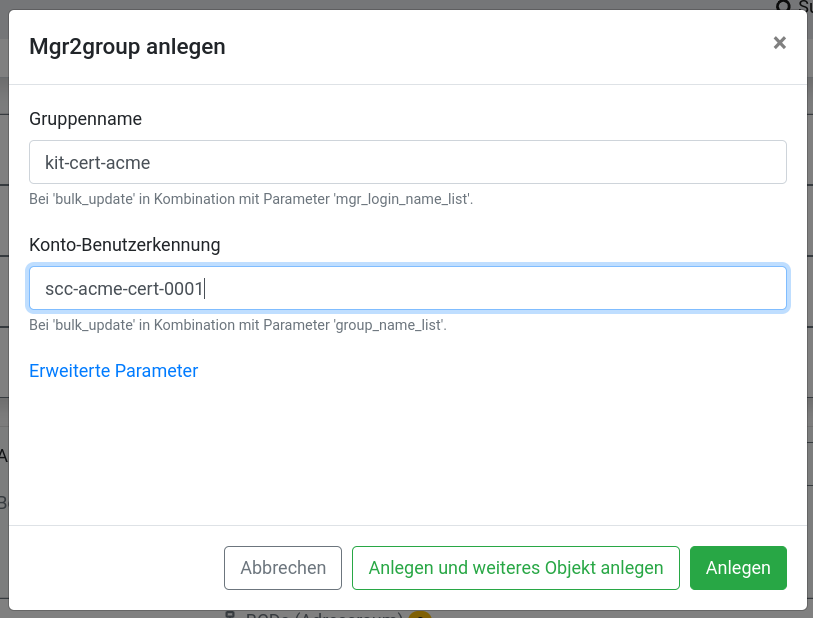
- Add your Service Account as Group Member (Gruppenmitglieder → +)
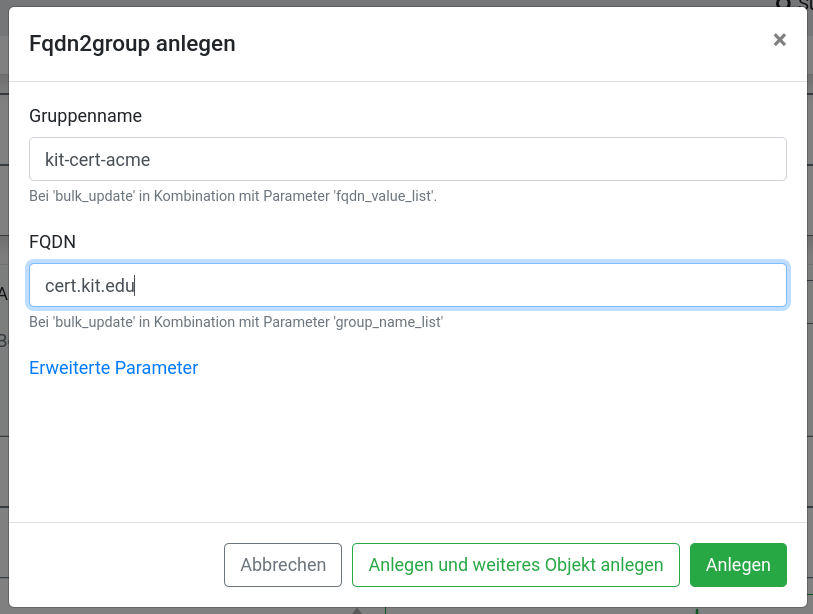
- Add Domains to your Group (Domains → +)
Creating Tokens
Note
All steps happen on the Serviceaccount, not on your normal account
- Log in to NETVS using the Serviceaccount (you can use the »incognito mode« of your browser)
- In the upper right, click on your service account name and then »Unterkonten & API-Tokens«
- Click on »Unterkonto erstellen«
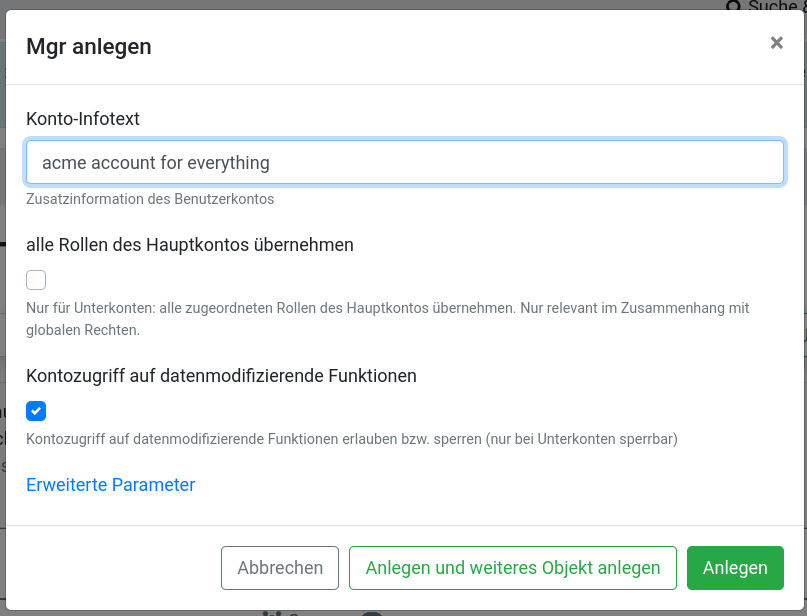
- Add a nice description
- Deactivate “alle Rollen übernehmen”
- Activate (don’t change preset) “Kontozugriff auf datenmodifizierende Funktionen”
- Open the newly created subaccount, go to »Tokens«, click on »+«
- Add a description, click on »Anlegen«, run the transaction
- You now have a token (but without permissions).
Add at least one subgroup
Note
All steps happen on the Serviceaccount, not on your normal account
- Now, create a subgroup (Untergruppen → »Neue Untergruppe anlegen und beitreten«)
- Depending on your permission management, there are two ways:
- Create a group for every domain or server.
- Un-Tick »Zuordnungen der Hauptgruppe übernehmen«
- Add domains to the subgroup (as in the previous step)
- Create one group to rule them all. Leave the tick at »Zuordnungen der Hauptgruppe übernehmen«
Assign permission to the subaccount
Note
All steps happen on the Serviceaccount, not on your normal account
- You must add the subaccount to the right subgroup.
- Copy the subaccount ID (Pattern:
XXXXXXXXXXX==[SUBM]) - Go to the Groups, select the previously created subgroup.
- Click on Mitglieder and »+«
- Paste the subaccount ID into »Konto-Benutzerkennung«